Note: All answers assume that you are a registered user and logged in.
Q: How do I save a new AHP hierarchy definition?
A: In the Session Administration Menu click on New.
The hierarchy window is displayed. Define a new hierarchy in the text input field and click on Submit new hierarchy, then Save in the Hierarchy Input Menu.
The group session window will open. Optionally provide a project short description and click Go, and the defined hierarchy is stored and shown as type “H” (Hierarchy) in the project table of the Session Administration Menu.
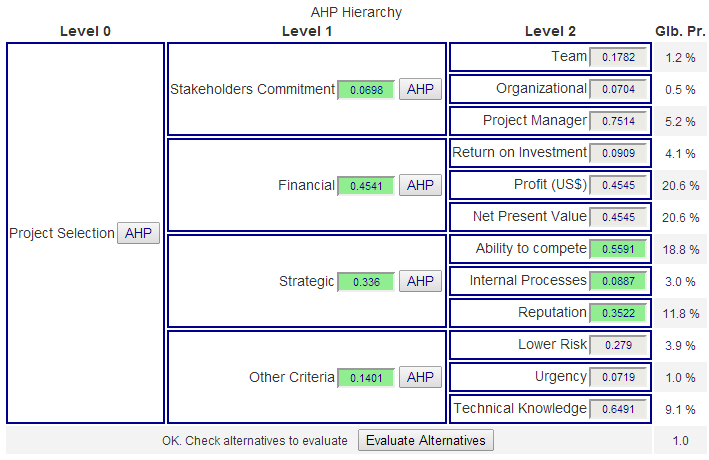
Q: How can I define and store a project for the evaluation of alternatives?
A: Start with a hierarchy definition, save and resume from the project table by clicking on the session code link. Complete all pairwise comparisons (Click on AHP in the hierarchy) to define the weights of criteria. (Before alternatives can be evaluated, criteria weights need to be defined.) Submit for group evaluation and view the result. In the group result page click on Use consol. priorities.
Then click on Evaluate Alternatives in the decision hierarchy display. Provide number and names of your alternatives and save a new project. It will be saved as type “A” (Alternative Evaluation). From there you can resume and start the alternative evaluation.
Q: How can I use a defined and stored hierarchy definition as template for a new project or new group session?
A: Click on the session code link of the project, you want to use, in the Stored AHP project session table.
a) If the project has no participants, the project will be opened in the group session input mode. Click on Leave, then Close in the Active Session Menu.
b) If the project has participants, the project will be opened in the AHP Group result window. Click on the Resume link at the bottom of the page, then Leave and Close in the Active Session Menu as in a).
You can now re-use the hierarchy definition and save as a new project.
 Operating your own website or blog, you will soon realize lots of comments with nonsense content and embedded links to obscure websites. These are comment spammers making your life difficult. Everyday you have to clean up or moderate all comments. In the past I used a wordpress plugin “spam free wordpress” to protect my blog, and for long time it was working fine without any problems. Writing a comment to my postings, you were asked to copy and paste a password from one to another field in the comment form. Suddenly it was not working any longer, and I found out that the developer changed his policy: I have to pay a license fee.
Operating your own website or blog, you will soon realize lots of comments with nonsense content and embedded links to obscure websites. These are comment spammers making your life difficult. Everyday you have to clean up or moderate all comments. In the past I used a wordpress plugin “spam free wordpress” to protect my blog, and for long time it was working fine without any problems. Writing a comment to my postings, you were asked to copy and paste a password from one to another field in the comment form. Suddenly it was not working any longer, and I found out that the developer changed his policy: I have to pay a license fee. 


